I N F O S E C
Vooki Android App Vulnerability Scanner
Vooki - Android Application APK Vulnerability scanner
Vooki AAS is committed to offering an extensive scanning approach, combining the precision of automated techniques with the thoroughness of manual methods. This dynamic duo of scanning strategies ensures a detailed and comprehensive vulnerability assessment, making it an indispensable ally for securing Android applications.
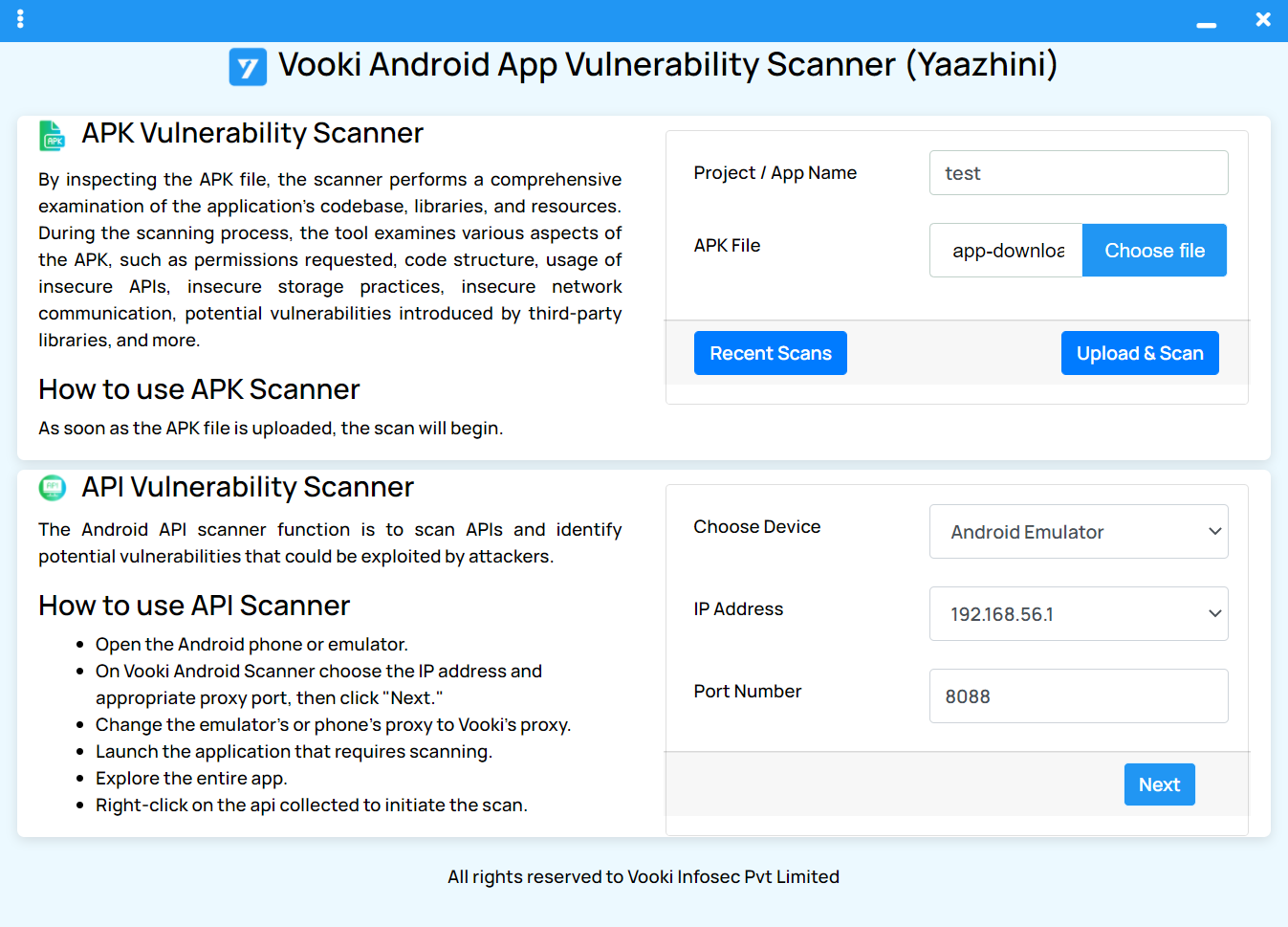
- Launch the Application: Begin by starting the Vooki application on your device, ready to initiate a secure scanning process.
- Project Naming: Efficiently organize your scans by providing a unique name for each project. This step ensures you can easily locate and review your scanning projects later.
- APK File Selection: Navigate through your device's storage and select the Android APK file you wish to scrutinize for vulnerabilities. Vooki is designed to support a wide range of APK files, providing versatility in scanning various applications.
- Initiate Scan: With the APK file selected, click on the
Upload & Scanbutton. This action triggers Vooki's powerful scanning engine to meticulously analyze the chosen APK file, searching for potential vulnerabilities. - Review Detailed Reports: Upon completion of the scanning process, Vooki presents a detailed report of all identified vulnerabilities. Each report is comprehensive, providing in-depth insights into the vulnerabilities detected in the scanned APK file, enabling users to understand and address security issues effectively.
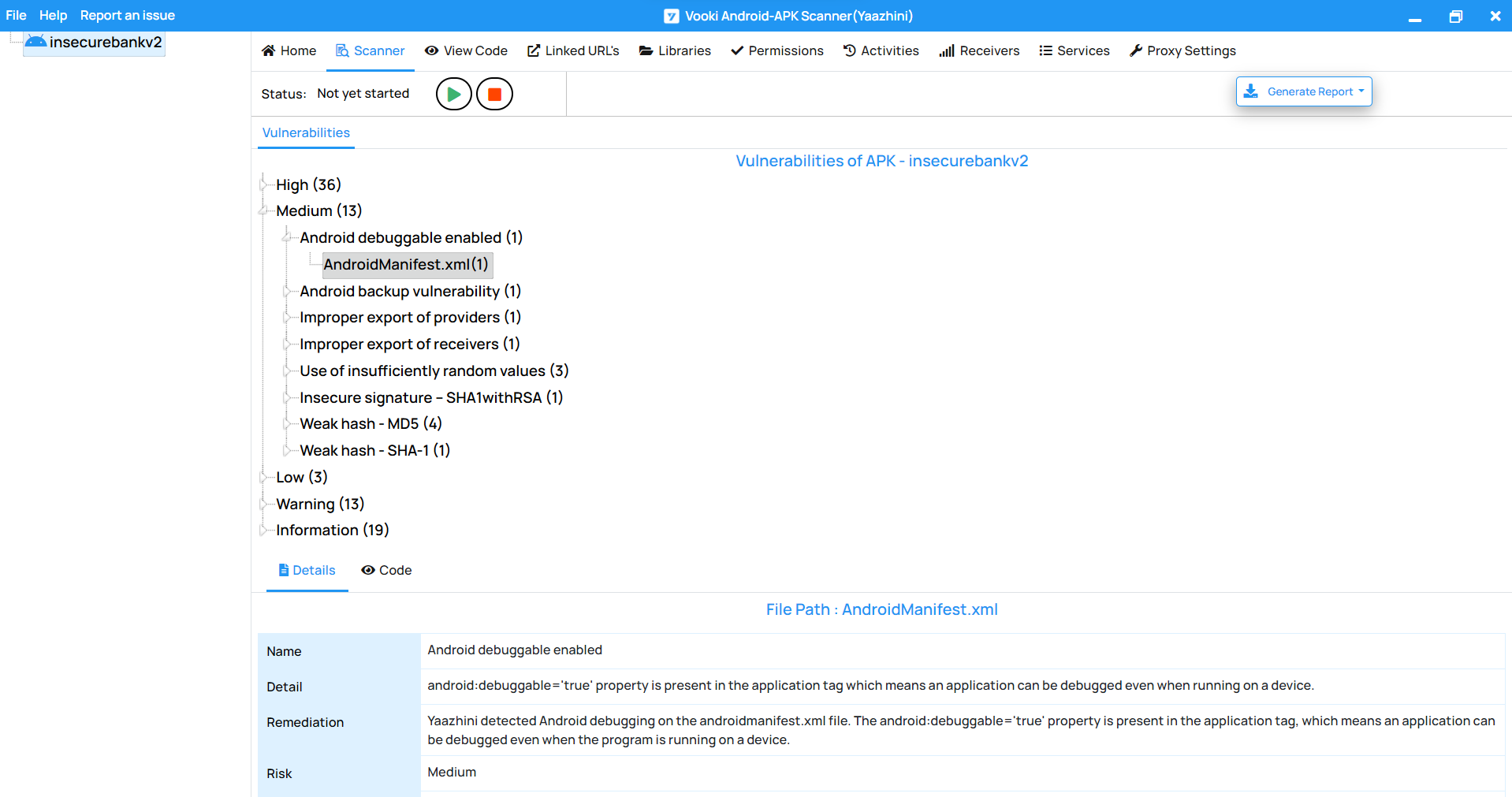
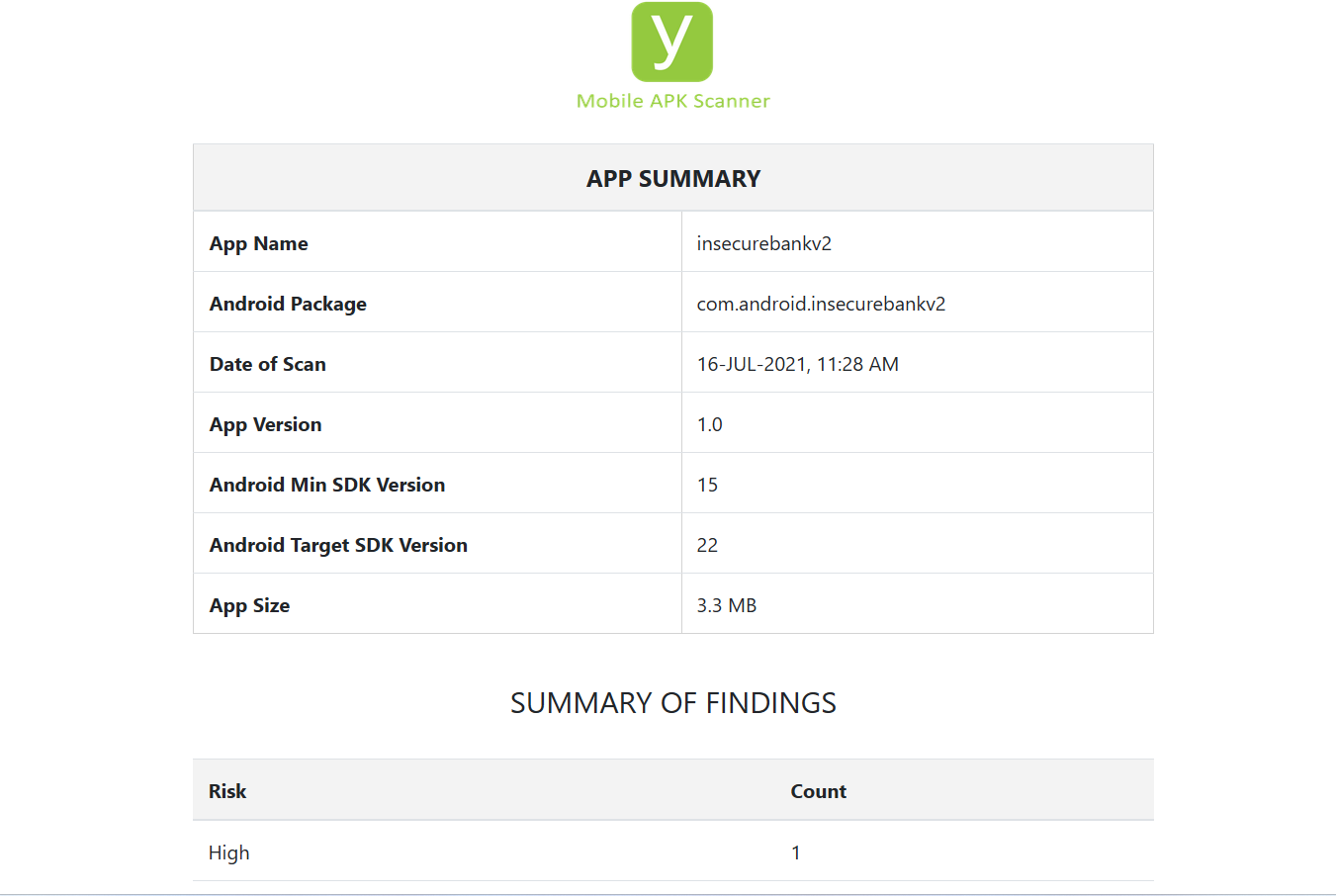
The Sample Report generated by Vooki’s Android APK Vulnerability Scanner initiates with a concise summary, offering a snapshot of all identified findings and their respective risk ratings. These ratings are meticulously assessed and assigned based on the recognized OWASP severity levels, ensuring that each finding is accurately evaluated for risk.
Each identified vulnerability within the report isn’t merely listed; it is accompanied by a thorough explanation. This detailed analysis offers insights into the risk associated with each vulnerability, providing a clear understanding of the potential threats they pose to your Android application.
Vooki-Android APK Scanner Sample Report.Vooki AAS REST API Vulnerability Scanner
With the Vooki AAS REST API Vulnerability Scanner, you can confidently navigate through your REST API’s security landscape, identifying and addressing vulnerabilities with precision and ease. Experience security that’s not just advanced but also user-friendly, turning the tedious process of manual vulnerability identification into a task of simplicity and ease.
- Launch Vooki Application: Kickstart the process by opening the Vooki application on your device, establishing the gateway to robust API security.
- Select Device Type: Specify the type of device you’re working with within the application. Vooki is designed to be versatile, catering to a broad range of device types for optimal user experience.
- Input PORT Number: For the incoming proxy, provide the relevant PORT number. This crucial step sets up the communication channel, allowing for seamless interaction between your device and the Vooki tool.
- Advance to Next Step: With the PORT number in place, click on
the
Nextbutton. This action prepares the Vooki tool to receive and process the data from your device, marking the commencement of the security scanning process. - Set Device Proxy to Vooki: Adjust the proxy settings of your device to align with the Vooki tool. Then, navigate through your application. This step ensures that the Vooki tool can efficiently monitor and analyze the data traffic, laying the groundwork for accurate vulnerability scanning.
- Initiate Scan: Upon spotting a node appearing on the Vooki tool, right-click on it. A ‘Scan’ button will appear; clicking on this button will trigger the Vooki tool to begin its meticulous scanning process, delving deep into the node to identify and highlight potential security vulnerabilities.
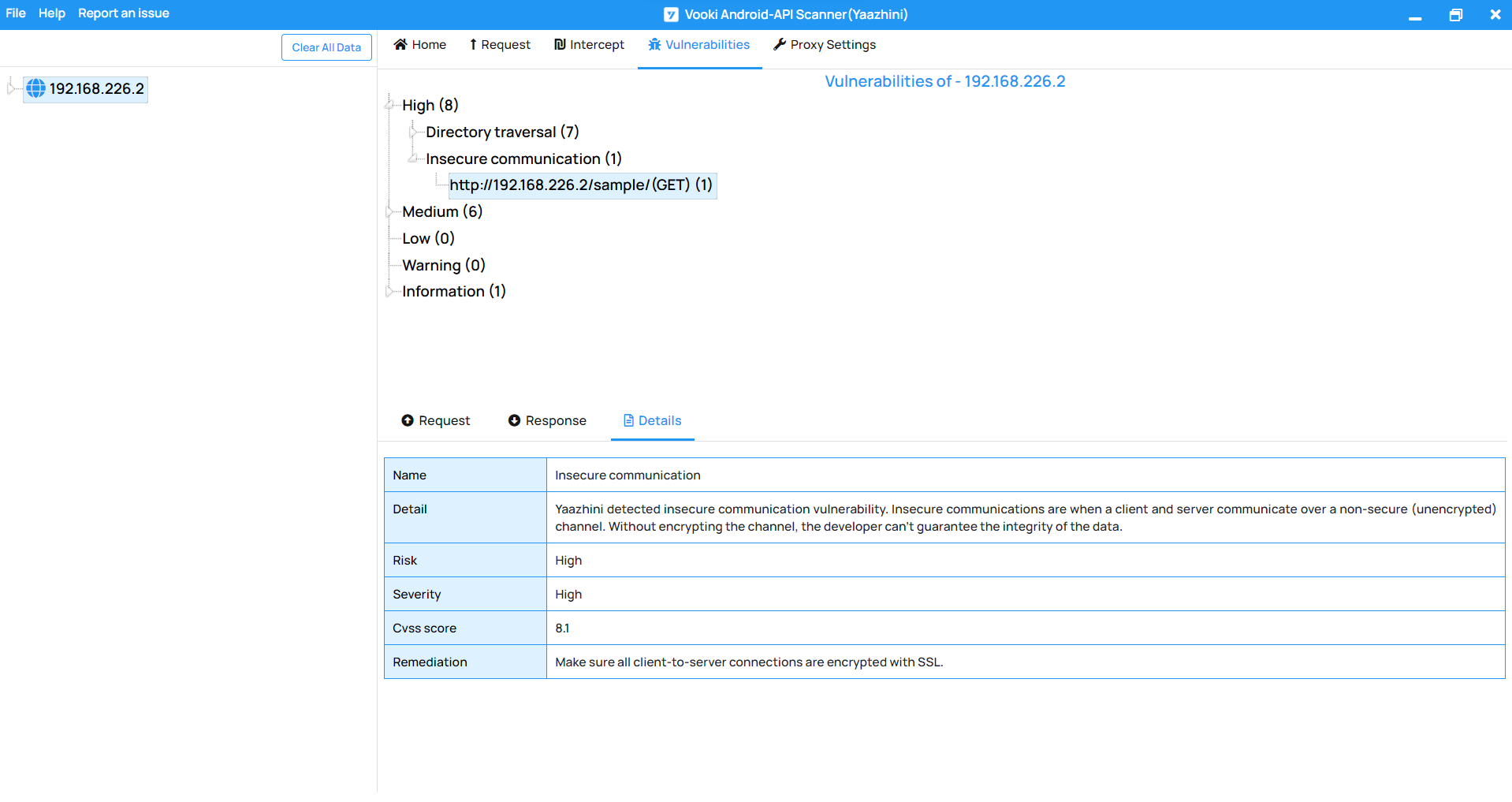
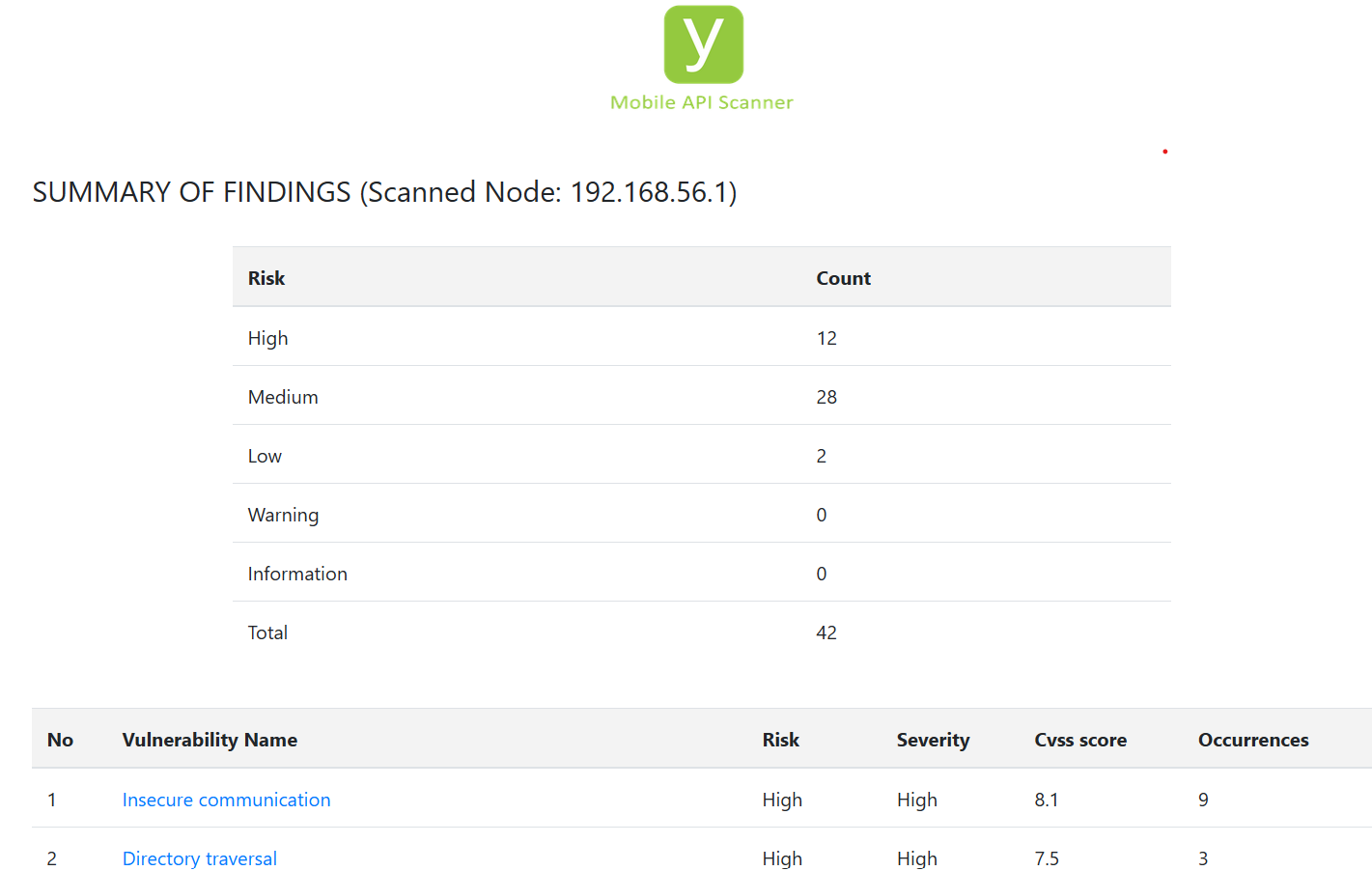
The Sample Report generated by Vooki’s Android API Vulnerability Scanner initiates with a concise summary, offering a snapshot of all identified findings and their respective risk ratings. These ratings are meticulously assessed and assigned based on the recognized OWASP severity levels, ensuring that each finding is accurately evaluated for risk.
Each identified vulnerability within the report isn’t merely listed; it is accompanied by a thorough explanation. This detailed analysis offers insights into the risk associated with each vulnerability, providing a clear understanding of the potential threats they pose to your Android application.
Vooki- Android Application Scanner REST API Sample Report.